Scenario
Make: Dell Switches
Model: N4032, N2048, etc
Server: Radius Server 2012, 2016, 2019
Description: This article is to discuss and show stepwise method of how to configure Radius authentication on Dell Switch stack using Radius Server. This configuration is valid for other Dell switch models as well.
Configuration On Switch
Step1: Configure aaa model on the switch
This is important to configure the aaa model on the switch to start Authentication, Authorization and Accounting. Execute the command as shown below.
edledge-switch(config)#aaa new-model
Step2: Configure aaa group and Radius Server
Configure radius group for authentication and authorization. Follow the command shown below.
edledge-switch(config)#aaa authentication enable EDL radius local
edledge-switch(config)#aaa authorization exec EDL radius local
You could use any name like “XYZ” or “ABC” etc, above “EDL” used as an example.
Step3: Add Radius Server Details On the Switch
Let us consider the IP address of the Radius Server is 10.1.1.11. Add the radius server details on the switch as shown below.
edledge-switch(config)#radius-server host 10.1.1.11
edledge-switch(config-auth-radius)#key edledge
Save this key somewhere. This key will used when the switch (host) will be added to the server.
All the required details of the radius server are added to the switch. Now it’s time to add the host (switch) to the server. Authentication policies are defined on the radius server which controls the client’s connection.
Configuration On Server
Step4: Access NPS Of Radius Server
RDP to the Radius Server and open Server Manager and then NPS. Follow the steps shown below.
mstsc ==> Radius server ==> Server Manager ==> Network Policy Server
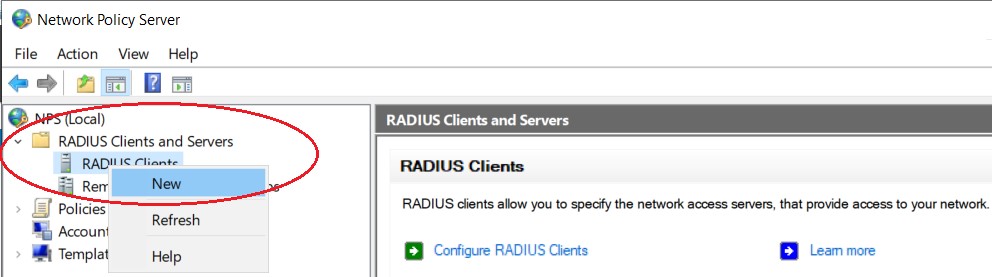
Step5: Add Host (Switch) to Radius Server
Right-click on “Radius Clients” and then click “New” to add the host to the server, as shown below.
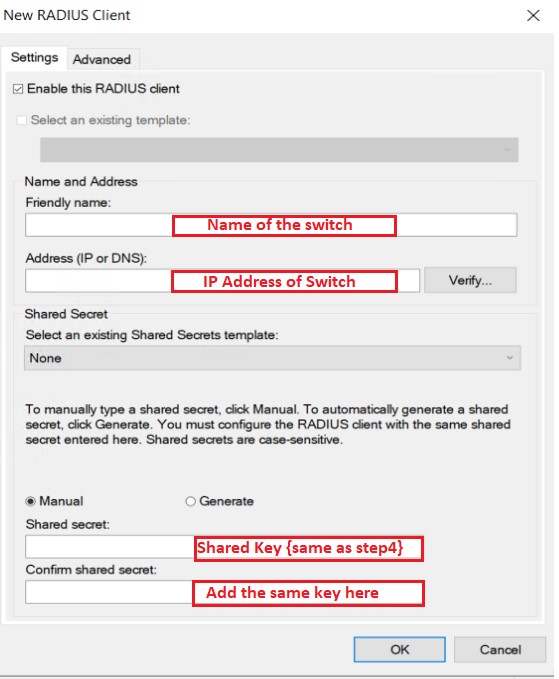
Step6: Add host (Switch) to the Radius server
Considering the Name of the switch is “edledge-switch“, IP address is “10.1.1.1” & Radius Key will be edledge [The same key we had used in Step 3]
Press "OK" to save.
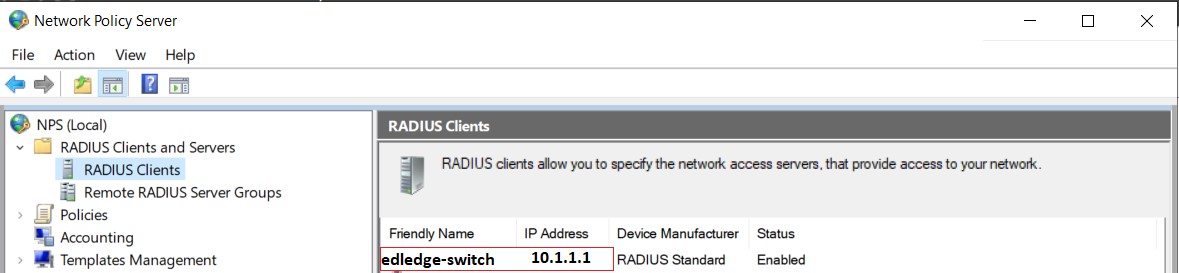
Step7: Ensure the host is successfully added to Radius Server.
The switch is ready to use Radius Authentication. Please note authentication policies need to define on the radius server which will be used by the host or switch and as per defined policies client’s authenticating will work.
Other Important Topics
- How to Change Radius Server Priority on Dell Switch
- RADIUS Bypass/Authorize/Unauthorize On DELL Switch Interface
- Radius Failover Configuration On Dell Switch
- Port-Channel/Channel Group Configuration – Dell Switches
- Dell N4000 Series Switch Stack Firmware Upgrade
Source: Dell, Lab, Knowledge Base.
EA00037