Scenario:
Make: Cisco
Model: WLC 2500 & Access Points 3800, 3700
Software Version: 7.6.x or later
Mode: CLI & GUI
Description: In this article, we will discuss in detail the cause, impact and solution of IDS Signature EAPOL Flood Attack on Cisco Wireless Access Points.
Understanding EAPOL & Impact
Details: EAPOL stands for Extensible Authentication Protocol over LAN. It is network port authentication used in IEEE 802.1X. A simple encapsulation that can run over LAN and is similar to the Extensible Authentication Protocol (EAP).
Impact: During an EAPOL flood attack, a hacker floods the air with EAPOL frames that contain 802.1X authentication requests. As a result, the 802.1X authentication server cannot respond to all of the requests and fails to send successful authentication responses to valid clients. The result is a denial of service to all affected clients. When the EAPOL flood signature is used to detect such an attack, the access point waits until the maximum number of allowed EAPOL packets is exceeded. It then alerts the controller and proceeds with the appropriate mitigation.
An example of the EAPOL flood attack log is shown below.
1458 |
Fri |
IDS Signature attack detected. Signature Type: Standard, Name: EAPOL flood, |
Solution
There are two ways to mitigate the issue of denial of authentication of clients due to the EAPOL attack.
1. Applied on Global Config [This is available on all versions of firmware]
2. Applied per WLAN [This is available on version 7.6 or later]
CLI Method
1. Global Config
Please note the changes made in global config mode will be implemented to all SSID that exist in the WLC.
Step1: Login to the controller and check the advance eap settings as shown below.
(Cisco Controller) >show advanced eap
EAP-Identity-Request Timeout (seconds)........... 30
EAP-Identity-Request Max Retries................. 2
EAP Key-Index for Dynamic WEP.................... 0
EAP Max-Login Ignore Identity Response........... enable
EAP-Request Timeout (seconds).................... 30
EAP-Request Max Retries.......................... 2
EAPOL-Key Timeout (milliseconds)................. 1000
EAPOL-Key Max Retries............................ 2
EAP-Broadcast Key Interval....................... 3600
RSN Capability Validation........................ enable
(Cisco Controller) >
Step2: Change the EAPOL Key Max Retires from default value 2 to 0. Follow the command to execute the change as shown below.
(Cisco Controller) > config advanced eap eapol-key-retries 0
Step3: Apply & Save the changes.
2. Per WLAN Config
Per WLAN config changes will be implemented to only selected WLAN. This needs to execute to all WLANs facing the EAPOL attack issue.
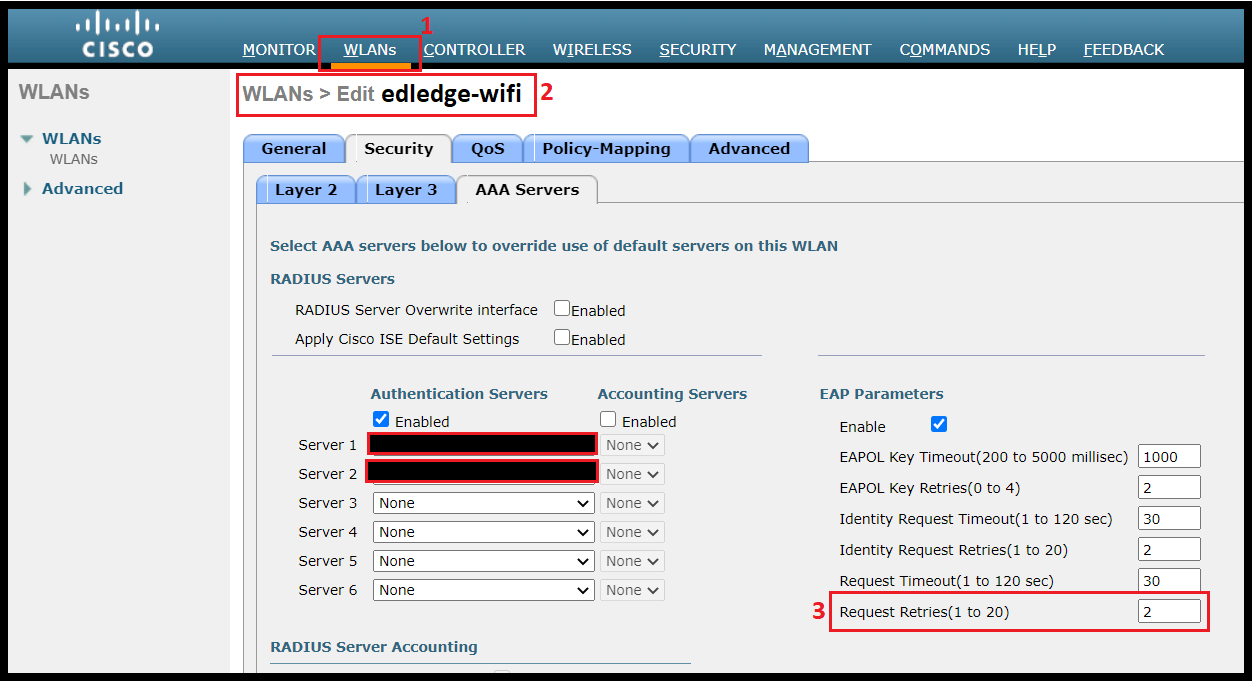
Step1: Follow the commands shown below and change the eapol-key-retries key to 0. Here edledge-wifi used as an example of WLAN ID.
(Cisco Controller) > config wlan security eap-params enable edledge-wifi
(Cisco Controller) > config wlan security eap-params eapol-key-retries 0 edledge-wifi
Step2: Apply & Save the changes.
GUI Method
1. Global Config
Please note the changes made in global config mode will be implemented to all SSID that exist in the WLC.
Step1: Login to the controller via GUI and go to the advance settings as shown below.
Step2: Follow the steps shown below and change the EAPOL Key Max Retires from default value 2 to 0.
Step3: Apply & Save the changes.
2. Per WLAN Config
As the name suggests, changes will be implemented to only selected WLAN. This needs to execute for all WLANs facing the EAPoL attack issue.
Step1: Login to the WLC and go to advanced settings as shown below.
Step2: Navigate to the WLAN ID for which changes need to be done and then change the EAPOL Key Max Retires from default value 2 to 0. Here edledge-wifi WLAN is taken as an example.
Step3: Apply & Save the changes.
There are a few alternatives Cisco Wireless solution available and they are good as well. I have personally worked on Ubiquiti Unifi Wireless Solution and they are working fine. Almost every feature is available with Ubiquiti. Do not forget to refer to the article if you are looking to reset Cisco WLC to factory default settings.
Source: Knowledge Base, Lab, Internet, Cisco
EA00047