Scenario
Switch: Cisco 2960, 3650, etc
Server: Radius Server 2012, 2016, 2019
Description: Configuration of Two Radius Server on Cisco Switch for Radius Fail-over. This configuration is valid for other Cisco switches as well.
Step1: Configure aaa model on the switch to allow AAA
This is important to configure the aaa model on the switch to allow Radius to control Authentication, Authorization, and Accounting.
edledge-switch(config)#aaa new-modelStep2: Configure the aaa group and add both Radius Servers
Once aaa model is configured now we would need to configure the radius group of the Radius server.
Radius Server 1 - edledge-radius01
edledge-switch (config)#aaa group server radius EDL
edledge-switch (config-edledge-radius)# server name edledge-radius01
edledge-switch (config-edledge-radius)# deadtime 1
Radius Server 2 - edledge-radius02
edledge-switch (config)#aaa group server radius EDL
edledge-switch (config-edledge-radius)# server name edledge-radius02
edledge-switch (config-edledge-radius)# deadtime 1
Step3: Configure Authentication, Authorization & Accounting
edledge-switch (config)#aaa authentication login default local group EDL
edledge-switch (config)#aaa authentication dot1x default group EDL
edledge-switch (config)#aaa authorization network default group EDL
edledge-switch (config)#aaa accounting dot1x default start-stop group EDL
Step4: Now Configure Both Radius Server Details On the Switch
Radius Server 1 - edledge-radius01
edledge-switch (config)#radius server edledge-radius01
edledge-switch (config-radius-server)#address ipv4 10.1.11.11 auth-port 1812 acct-port 1813
edledge-switch (config-radius-server)# key edledge
Radius Server 2 - edledge-radius02
edledge-switch (config)#radius server edledge-radius02
edledge-switch (config-radius-server)#address ipv4 10.2.11.11 auth-port 1812 acct-port 1813
edledge-switch (config-radius-server)# key edledge
Save both keys,as same key will be used when this switch (host) will be added to the server.
Step5: Now check and ensure both Radius Servers are added to the Radius group EDL
aaa group server radius EDL
server name edledge-radius01
server name edledge-radius02
deadtime 1
Now time to add a host (switch) to the server so that the Radius server starts authenticating hosts as per Radius Policies.
Step6: Login to Radius server and open Server Manager and then NPS
mstsc ==>Radius server ==> Server Manager ==> Network Policy ServerStep7: Add Host (Switch) to Radius Server 1
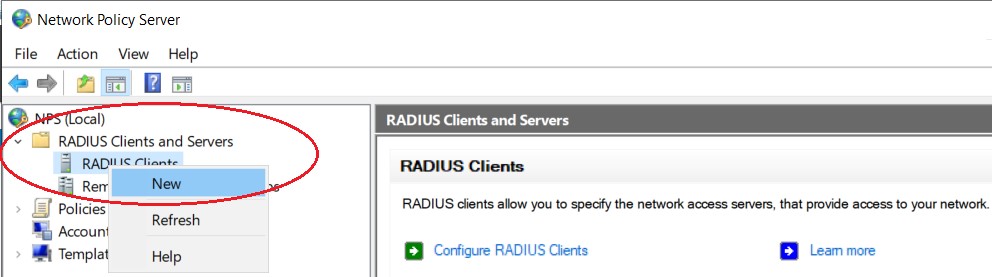
Right click on "Radius Clients" and then click "New"
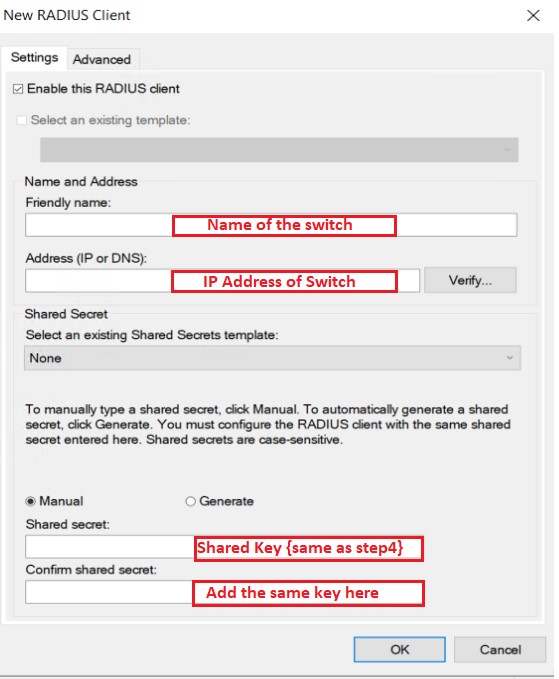
Step8: Add host (Switch) to the Radius server
Name of the switch-edledge-switch
IP address of the switch - 10.1.1.1
Key - The same key we had used in Step 4 [edledge]
Press"OK"to save.
Step9: Repeat Step8 on Radius Server 2 to add host {switch} details on Radius Server 2
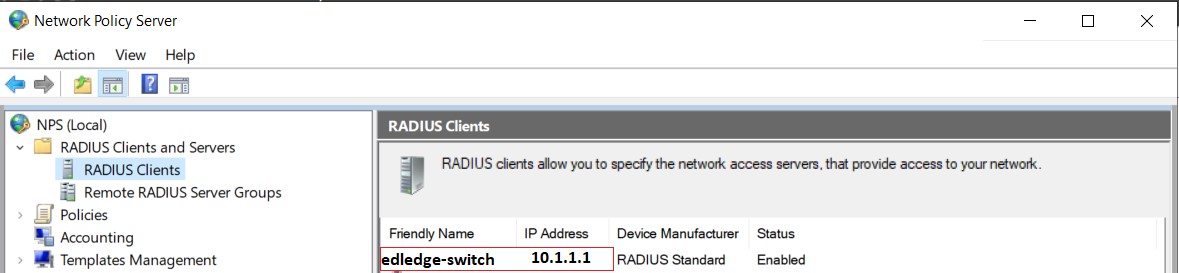
Step10: Ensure hostname with correct IP is now visible in the host file name of both Radius Servers {Radius Server 1 & Radius Server 2}
The switch is all for the test set and added to the Radius server. Make sure the switch is able to ping the Radius server and once Policies are added to the Server, we are good to go. Standalone Radius configuration on the Cisco switch for authentication is explained in the attached article.
Source: Cisco, Lab, Knowledge Base
EA00022