Scenario:
Make: Cisco
Model: ASA 5506-X, ASA 5506 W-X, ASA 5508-X, Cisco ASA 5500 Series
Mode: GUI & CLI
Version: ASA version 9.x or later, ASDM version 7.x or later
Description: In this article, we will discuss the stepwise method of how to configure IP SLA on Cisco ASA Firewalls. IP SLA can be used to configure Redundant or Backup ISP links on Cisco ASA Firewalls. Refer to the article to know the steps to configure Redundant or Backup Links on Cisco via CLI & configure Redundant or Backup Links on Cisco via GUI.
Introduction
IP SLA is an active method of monitoring and reliably reporting on network performance. IP SLA generates and actively monitor traffic continuously across the network. An IP SLA Router is capable of generating traffic and reporting on it in real time.
CLI Method
Step1: Login
SSH onto the ASA using username & password.
Step2: WAN Interfaces
Configure both WAN links on two different interfaces of the ASA. You could name those two interfaces as “outside” and “backup“.
edledge-asa#
edledge-asa# conf t
edledge-asa(config-if)# interface GigabitEthernet0/1
edledge-asa(config-if)# nameif outside
edledge-asa(config-if)# security-level 0
edledge-asa(config-if)# ip address 11.22.33.44 255.255.255.0
edledge-asa(config-if)# exit
edledge-asa#
edledge-asa#
edledge-asa# conf t
edledge-asa(config-if)# interface GigabitEthernet0/2
edledge-asa(config-if)# nameif backup
edledge-asa(config-if)# security-level 0
edledge-asa(config-if)# ip address 11.22.11.44 255.255.255.0
edledge-asa(config-if)# exit
edledge-asa#
[ays_quiz id=’2′]
Step3: Add Route with Tracking
Add route for both “outside” (Primary Link) and “backup” (Secondary Link)
edledge-asa#
edledge-asa# conf t
edledge-asa(config-if)# route outside 0.0.0.0 0.0.0.0 11.22.33.1 1 track 1
edledge-asa#
edledge-asa# conf t
edledge-asa(config-if)# route outside 0.0.0.0 0.0.0.0 11.22.11.1 254
Step4: Monitoring Option
Configure a new monitoring process with ID 123. Add the monitoring protocol and the target network object whose availability the tracking process monitors. Specify the number of packets to be sent with each poll. Specify the rate at which the monitor process repeats (in seconds).
edledge-asa#
edledge-asa# conf t
edledge-asa(config-if)# sla monitor 123
edledge-asa(config-sla-monitor)# type echo protocol ipIcmpEcho 8.8.8.8 interface outside
edledge-asa(config-sla-monitor)# num-packets 3
edledge-asa(config-sla-monitor)# frequency 10
edledge-asa#
edledge-asa# conf t
edledge-asa(config-if)# sla monitor schedule 123 life forever start-time now
edledge-asa#
edledge-asa# conf t
edledge-asa(config-if)# track 1 rtr 123 reachability
edledge-asa(config-if)# exit
edledge-asa(config)# exit
edledge-asa#
Step5: Verify Configuration
Verify the configuration and ensure routing is added.
edledge-asa# show running-config sla monitor
sla monitor 123
type echo protocol ipIcmpEcho 8.8.8.8 interface outside
num-packets 3
frequency 10
sla monitor schedule 123 life forever start-time now
GUI Method
Step1: Login
Log in to the ASA using username & password.
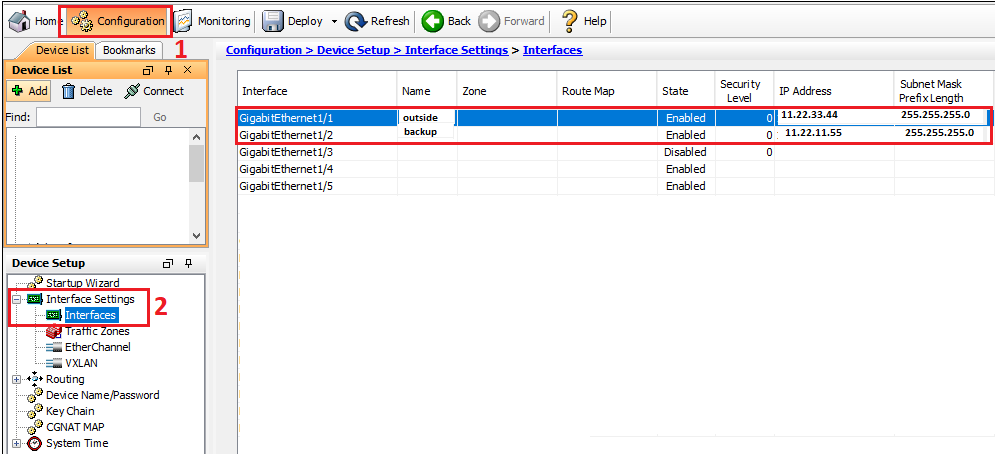
Step2: WAN Interfaces
Configure both WAN links on two different interfaces of the ASA. You could name those two interfaces as “outside” and “backup“.
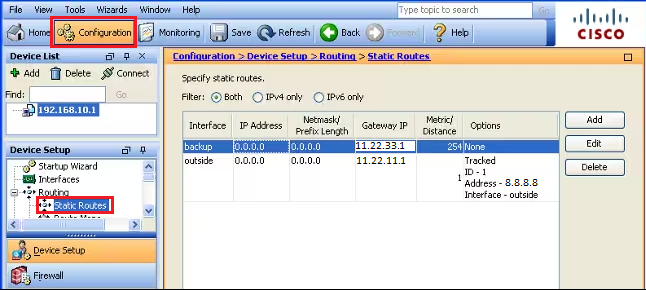
Step3: Routing
Add static routing for the Primary Internet line [WAN]. Here in this case, “outside” interface is the primary WAN, and “backup” is the secondary WAN. Follow the steps as shown below in the image.
Step4: Tracking
While adding a route for the primary WAN, add tracing, and follow the steps as shown below.
Step5: Monitoring Option
While adding static route and tracking, click “Monitoring Options” in the previous step and add monitoring details as per requirement.
Step6: Routing for Secondary WAN
Add the static route of secondary WAN and keep the matrix to a maximum (recommended is 254).
Step7: Verify Configuration
Verify the configuration and ensure routing is added.
IP SLA is configured on Cisco ASA.
Other important topics
- How to Configure VPN Between Microsoft Azure & Cisco ASA
- Add Static ARP or MAC Binding on Cisco ASA Firewall
- Cisco Firewall or ASA Active/Standby Failover Configuration
- Cisco ASA IOS Upgrade/Downgrade GUI
- Configure SSH On Cisco ASA Firewall CLI
Source: Knowledge Base, Internet, Cisco
EA00129